OSCP Tips and Tricks
My OSCP journey is finally over and I have a lot of people to thank for inspiring me to finish it. Most of all I have Dylan to thank. I highly recommend you check out his blog and see his own journey. This article is intended to have all the information about OSCP that I wish I had when I first started studying for it. I’ve tried a large number of popular study materials and I review each one of them here, as well as share miscellaneous tips and opinions about the exam.
Exam Prep
My Background
I work full-time as a junior red team consultant at a big company now, but I began studying for the OSCP at the end of my junior year of college. At that point I had the Security+ and the Cybersecurity Analyst+ certifications already from CompTIA, which are purely blue-team oriented. My hands-on experience with cybersecurity then was limited to just clubs and competitions.
My Roadmap
Overall, the path from having pwned zero boxes to getting OSCP took me about a year. My certification prep philosophy is all about using overlapping study materials to eliminate any gaps in my knowledge and I followed it once again for OSCP. I used the TjNull OSCP-like list of machines as a rubric and then ventured into other resources after I completed most of it. You can see the rough outline of my roadmap on the image below.
Disclaimer: I studied for OSCP while being full-time in university and doing intensive cyber competitions, as well as balancing family and friends. If you have the time to study for OSCP full-time, it will take you less than a year.

- Windows & Linux Privilege Escalation for OSCP and Beyond and their associated TryHackMe rooms took me just a few days, but left me with a solid grasp of the fundamentals of privilege escalation.
- HackTheBox took me about 6 months to get through just because of the sheer volume of boxes to root and because it took me some practice before I could solve machines within a reasonable amount of time.
- I worked through Proving Grounds Practice machines for about 2 months before Offsec screwed up my billing and left me without lab access despite charging me for it.
- I spent 2 months going through Virtual Hacking Labs, at which point I started to realize that I’m picking up on attack paths pretty quick and might be ready to take the exam soon.
- I felt like I was still lacking in the Active Directory department, so I bought a month of CyberSecLabs for their AD labs. I ended up finishing all of them in just a few days and knew it was time.
- When July rolled around I finally bought my course access and after about a week of going through the labs I realized that I don’t want to wait any longer and I just booked the exam for the week after.
Courses and Labs
This section goes into detail about every study resource I used, but if you just want the TL;DR of it, you can refer to the following table with my ratings for them all:
| Study Resource | Exam Applicability | Fun | Value for Money | Total Score |
|---|---|---|---|---|
| Tib3rius Courses | 5/5 | 4/5 | 5/5 | 93% |
| HackTheBox | 4/5 | 5/5 | 5/5 | 93% |
| Proving Grounds | 5/5 | 3/5 | 4/5 | 80% |
| CyberSecLabs AD | 3/5 | 4/5 | 4/5 | 73% |
| Virtual Hacking Labs | 4/5 | 2/5 | 2/5 | 46% |
Tib3rius Courses (THM)
Tib3rius has several high-quality courses on Udemy, which have companion TryHackMe rooms:
- Udemy - Windows Privilege Escalation for OSCP & Beyond
- Udemy - Linux Privilege Escalation for OSCP & Beyond
The course videos definitely do the job and have minimal flare to them. The slides are very clear and follow the same format I personally take notes in. The associated TryHackMe rooms are also well made, but unfortunately are meant to give you experience exploiting privilege escalation vulnerabilities rather than actually finding them.
Exam Applicability Every privesc I achieved within the OSCP exam was covered by Tib3rius’s courses. It’s not necessarily because he teaches things that will specifically occur on the OSCP, but because he teaches an all-encompassing methodology that will cover pretty much every possible attack path in general. It will help you tremendously.
Value for Money I was debating giving this a 6 out of 5, because the value you get is ridiculous compared to the price you pay for it. I snagged both of these courses on sale for 10 bucks a piece and Tib3rius constantly runs promotions where he posts discount coupons on his Twitter account. You get several hours of high-quality video content and the associated TryHackMe rooms are totally free.
HackTheBox (HTB)
HackTheBox needs no introduction. I believe that although HackTheBox doesn’t accurately reflect what you’ll see on the OSCP exam, it is still the best platform to practice and learn for it. You learn how to think creatively, how to be thorough and get to see many different unique vulnerabilities and misconfigurations.

Exam Applicability A lot of people ask if OSCP is harder than HackTheBox. The answer is both yes and no. Most HackTheBox attacks on even active easy boxes are harder than OSCP, however HackTheBox machines rarely have 20+ ports with real services running. Despite that, I feel like the experience gained from HackTheBox is still invaluable in OSCP.
I especially recommend that you do the following Active Directory machines to practice for OSCP:
- Easy: Active, Forest, Sauna
- Medium: Cascade, Resolute
- Hard: Blackfield
Value for Money For the low price of a VIP you get access to literal hundreds of high-quality boxes. There is no other study resource that can match the sheer volume offered by HackTheBox. Beyond even OSCP-like machines, some of the active boxes are a ton of fun and there’s also retired fortresses and endgame networks for you to attack once you have the basics down.
Proving Grounds (PG)
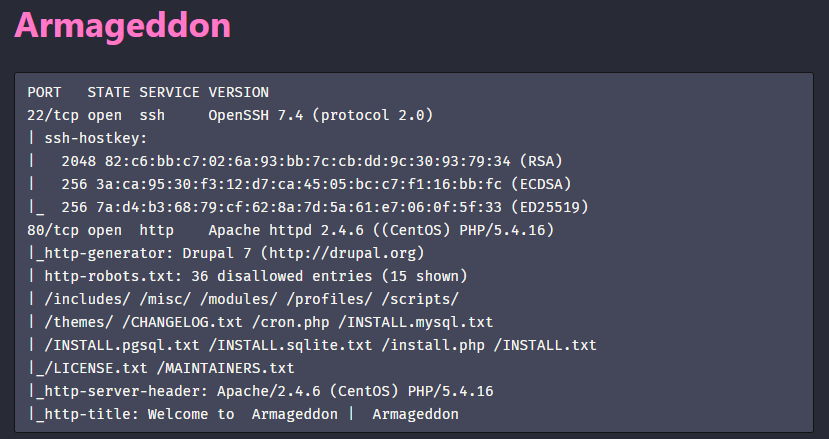
Offsec are behind Proving Grounds, so unsurprisingly it’s one of the best resources for practicing before OSCP. The machines are decent and the price is unlike that of the PWK. For the reasons listed in the next section, I recommend that you do Proving Grounds as the final stage of your exam prep.

Exam Applicability Proving Grounds machines are hands-down the most accurate representation of systems you’ll see on the OSCP. Just like exam machines, most PG boxes have tons of ports open with real services running on them and have strict outbound firewall rules that only allow reverse shells to come in through certain ports. If anything, I even found some of the PG machines to be more difficult than the exam ones.
P.S - skip Butch or you’ll regret it
Value for Money Proving Grounds has a sizeable selection of machines of varying difficulty levels to go through. If you are planning to take OSCP, you can’t miss it. That said, it lacks the level of polish of HackTheBox and the UI itself is certainly rough to say the least. Oh, and brace yourself for constant VPN issues.
VirtualHackingLabs (VHL)
VirtualHackingLabs is a course for beginners that comes with a PDF and a certificate of completion. Just skip it unless you have money to throw away. It might sometimes be an accurate representation of exam machines, but you’re better off paying for 5 months of PG for the price of a single month in VHL.

Exam Applicability If you are used to elaborate attack paths from HackTheBox, you will be severely disappointed when doing VHL, because its machines are all very boring and methodical, which is precisely how OSCP machines are. I have found that the Advanced and the Advanced+ difficulty machines best reflect exam systems.
Value for Money VHL access will cost you 100 bucks a month and after completing most of the boxes there, I still have not figured out what justifies this crazy price. There are only 2 things this resource offers that others don’t:
- The PDF course
- The certificate of completion
Personally, I have not found either of these two factors enough to justify paying this much. I didn’t even bother filling out the reporting deliverable for the certificate of completion despite having pwned enough machines to get it.
CyberSecLabs (CSL)
I think that CSL is a respectible new player on the vulnerable lab market. The subscription is very affordable and the number of boxes you get access to is reasonable. The boxes they put out are all high quality and best of all, they offer Active Directory labs.

Exam Applicability Unfortunately, the CSL AD labs are far from what the OSCP AD is like. A significant part of the OSCP AD is post exploitation, so things like pivoting, credential dumping, etc. CSL AD labs are independent domain controllers, so you don’t get any practice with that. They help nail some of the fundamental AD exploits, but fall short of providing an all-encompassing experience.
Value for Money CyberSecLabs is a pretty good resource for those just starting out with hacking and their boxes are extremely well made. If you are on the more experienced side, you might find it too easy though. It’s something I’d definitely recommend and the only reason it doesn’t get a 5 like HackTheBox is because it’s arsenal of machines is limited.
Pentesting With Kali (PWK)
I will refrain from commenting on the PWK course itself besides my personal reasoning for not spending time on the labs. After a whole year of intensive prep, and wanting to move onto red teaming asap, I felt that taking the entire 3 months would cost me more than failing. I felt ready, so I booked the exam.

Thoughts on Extra Credit If you are doing all the exercises purely for learning sake, all power to you. If you are thinking about doing the lab report for the 10 extra points, I recommend that you consider what would be the best use of your time. There is a LOT of exercises to complete and document. Your lab report will probably end up in the hundreds of pages. Is that the best use of your time? Personally, I felt that my time was better spent doing more boxes.
Note Taking
One of the most important things you should do as you are preparing for OSCP is take notes for your personal knowledge base. It really doesn’t matter what note-taking software you use, whether it’s Obsidian, Typora, Sublime, Vim or Notepad. As long as your notes are coherent enough for you to understand them later, you are good.
Take notes on every single box you pwn. You don’t have to write a pentest report. You just need a few bullet points with key commands and their output. You’ll go through hundreds of vulnerabilities as you prep and some of them will inevitably end up on the exam. You’ll be thanking yourself when you already have steps you can follow during the exam.
Exam Time
Scheduling the Exam
Picking Time
If you have work on Monday, don’t schedule your exam for Sunday. Unfortunately, this is an example of “do as I say, not as I do”, because I did the exact opposite. Because I scheduled my exam on a week’s notice, there was no morning time slots available for Saturday morning. In fact, there wasn’t any time slots for Saturday morning for the 3 foreseeable months, so either book your exam way in advance or prepare to take leave from work for a day or two. The exam left me exhausted and I had only 3 hours of sleep before going to work. After getting home from a full day of work I still had to finish my report and I cannot remember the last time I was this tired.
Last Minute Prep
I can’t think of anything you can possibly spend your time on, the day before your exam, that will be more helpful than rest. As long as your devices and notes are in order, you shouldn’t be doing any last minute cramming. There’s a reason athletes avoid overtraining just before competition - it’s because you’ll be much better off when you are fully rested. For the day before your exam there is only 1 important goal - get enough sleep. Take melatonin if you are anxious and think you won’t be able to sleep well. Set your alarm and come into your exam fresh.
Proctoring Software
Spare Hardware
Heed my warning, lest you will suffer a most unfortunate end. Have a backup device to take the exam from.
My PC is on the higher end of specs, so I was confident that it could face any technical challenge I throw at it. I could not foresee just how much the Offsec proctoring software sucks. My peripherals would disconnect when I tried to share screens and after trying every possible browser, hardware configuration and setting, I had to do my exam from a laptop that had none of the tools I’m used to, and worst of all, was running an ARM Kali Linux VM. It is a sheer miracle that I managed to pass with the conditions I was working in, because not only did I lose an hour of time and a lot of morale to troubleshooting, but I also couldn’t compile any exploits for AMD64 Linux properly. Have a backup device in case something happens and have spare VM’s and clean snapshots for everything, so you don’t lose precious exam time if something blows up on you.
The Proctors
My proctors were pretty chill and weren’t ever a distraction to me. There were a few occasions when I forgot about them completely and began celebrating and swearing out loud. They didn’t mind. Only thing you cannot forget about is telling them when you leave your computer. If you step away without notifying them, they will report you to Offsec and they will investigate your exam activity logs before approving your certificate. And make sure to tell your family not to come into your room during the exam.
Exam Difficulty
Complexity
Penetration Testing is not considered an entry level field and neither is Cybersecurity in general. What we’re talking about here is a non-entry-level field of a non-entry-level field within technology. The mere fundamentals of pentesting might seem incomprehensively difficult to someone without experience, and they certainly did for me at first. However, the things you learn and do in the OSCP are the most rudimentary basics of pentesting. None of the techniques you need to employ on the exam even come close to some of the active medium-difficulty HackTheBox machines. If so, then why do so many people fail?
Rabbit Holes
I believe the reason the exam is still difficult is because you are given more possible attack paths than time. Your exploit might be a one-click GitHub script, but if there’s over 30 interesting ports open on the system, it will be a while before you even get to the port that’s vulnerable. Avoiding these pitfalls is absolutely the most helpful skill OSCP teaches you, because in a real pentest this issue is greatly exasperated by the fact that you might be dealing with hundreds or thousands of hosts. There’s no way you can possibly get through every port on every machine in time. You need to learn to triage and know when to dig deep and when to let go of an attack path.
Taking Breaks
If you are fixated on trying to exploit something, you’ll be much better off taking a break rather than trying to push through. Working without breaks leads to diminishing returns, because at some point you’ll be so tired that your performance is degraded enough to stop you in your tracks. If you take frequent breaks, you’ll have energy that lasts through more of the exam than it would if you didn’t. Moreover, it’s helpful to be distracted from the exam if you are stuck, because maybe you took a wrong turn and need to rethink your whole approach. That mental reset is important.
Reporting
Screenshots
Take screenshots religiously during your exam. You’ll be thankful you did later on when you start reporting. Don’t wait till an hour before the close of your exam to take screenshots. It took me several hours to replicate all attacks from scratch and document them in enough detail for the report. Double, triple, quadruple check that you have screenshots of all flags that you got. I didn’t blur any passwords within my screenshots just in case Offsec would want them, but if you are writing a real pentest report, you absolutely should.
My advice is to have a hotkey for full window screenshots. Cropping hundreds of screenshots may take time and you’ll end up procrastinating on screenshoting if you need to get out of your flow to do it. Incessantly taking screenshots allows you to stay in the zone while having all the documentation you need. You can use your reporting time to pick out the screenshots you need and crop them inside Word.
Report Template
You are free to roll up with a custom report template, as long as it has the sections required by Offsec. I was horrified by the appearance of the Offsec template, so I ported its sections to my own formatting. My template had the following section layout:
- Cover Page
- Table of Contents
- Introduction
- Objective
- Scope - what IP addresses were given to you?
- High-Level Summary - did you complete the objective?
- Recommendations - how can they fix reoccuring issues?
- Methodology
- Reconnaissance - listed recon tools
- Exploitation - listed ExploitDB and GitHub
- Privilege Escalation - listed PeasNG suite
- Post-Exploitation - listed pivoting tools
- Independent Challenges
- Target
- Open Ports
- Initial Access
- Severity - low, medium, high or critical
- Description - executive summary of the issue
- Mitigation - few bullet points on how to fix it
- Steps to Reproduce - thorough explanation
- Privilege Escalation
- Severity
- Description
- Mitigation
- Steps to Reproduce
- Target
- Active Directory
- Foothold Machine
- Open Ports
- Initial Access
- Severity
- Description
- Mitigation
- Steps to Reproduce
- Privilege Escalation
- Severity
- Description
- Mitigation
- Steps to Reproduce
- Post-Exploitation - credential dumping, pivoting, etc
- Second Machine
- Domain Controller
- Foothold Machine
Writing Process
I follow a pretty simple methodology for writing reports. I lay out my screenshots in chronological order of exploitation inside the document and then narrate them once I have the structure down. You’re not writing an essay for your English class, so your writing doesn’t need to be eloquent. It just needs to decribe what you did in as much detail as necessary for someone technical to replicate it.
Criticism
Pricing Changes
Any way to spin these changes in some benevolent light is straight up astroturfing. Students used to be able to buy course access for just 30 days and save some money on an already extremely expensive cert, but we lost that ability in March of 2022. You are now locked into the most expensive purchase option and your flexibility as well as savings associated with less lab time are eliminated. Additionally, lab extensions are now limited to push you towards buying the annual Learn One subscription. And finally, this is also compounded by the fact that the retake price for the exam went up. Call this whatever you want, but I call this wack.
Exam Stability
Some people will argue that without exception every exam failure is the student’s fault, however that is simply not true. Nobody is perfect and neither is the exam network. Active Directory is specifically known to have severe exam breaking issues that are thankfully fixable with box resets. If you are looking at BloodHound or dumping hashes and feel like you’re missing something and can’t move laterally because of it, just reset your environment.
- A friend of mine failed the exam because his foothold system was missing crucial user sessions, which then reappeared after a reset, which was very late into the exam, so it was already too late to pass at that point.
- My own AD was missing crucial group permissions, without which it wasn’t possible to pivot. Thankfully, I realized this early and only lost 2 hours beating my head into the desk trying to figure it out.
Moral of the story - reset the boxes if you think something isn’t right. If you have good notes you’ll get back in. Offsec still has some work to do in ensuring Active Directory works as intended on the exam.
Conclusion
So how does one pass OSCP? Try harder Just put the time in to study. Unless you are preparing for OSCP full-time, having a timetable of just a few months is not realistic. It took me about a year to get through my study materials and I highly recommend trying out as many as you can. At the very least, complete the TjNull’s OSCP-like HackTheBox list and preferably combine it with Proving Grounds. Take notes, take breaks, screenshot religiously and finally, have fun.