How to Start a CPTC Team
Collegiate Penetration Testing Competition is an amazing opportunity to experience penetration testing in its entirety, and I highly encourage participating to see if offensive security is a career for you. You need a team to participate in CPTC and this blogpost is meant to be a guide for schools that don’t have one yet, or are trying to revive one for next season. Last year my entire team from Cal Poly Pomona graduated, so I had to start from scratch and ended up building a team that won gold both internationally and in our own region. I want to share my leadership experience with others and hopefully inspire more people to participate in this competition.

Before you Start
What is CPTC?
CPTC is an offensive security consulting competition. Don’t think that it’s a CTF like many other competitions, because it is not. When you graduate and start a career in penetration testing or red teaming, you’ll quickly realize that your performance as a consultant is not limited to technical skill. You can be the world’s most talented hacker, but if you can’t effectively communicate your findings to a client and create value for them, you won’t be hired again. CPTC at the core is a technical competition, but it places a huge emphasis on consulting skills, therefore you need to be versed in both technical and business matters to win.
The following are the scored categories of CPTC that make up the total score of a team:
| Category | Description |
|---|---|
| Technical Findings | The score you get from the things you hack in the environment and communicate to the client. |
| Report Quality | The score you get from the penetration testing report you submit at the end of the competition. |
| Presentation | The score you get from presenting to the executive board of the client at the end of the competition. |
| Injects | The score you get from business tasks given by the client during the competition. |
| Client Interactions | The score you get from communicating with the client during the competition. |
| Violations | The score that is deducted from you for violations of scope or things like account lockouts. |
Is there a team already?
The first thing you need to do before you start assembling a CPTC team is to find out if there’s already a team at your school. CPTC limits participation to one team per school, therefore you should not start a team if one already exists. Start by looking at the list of teams that participated in the previous season and if you don’t see your school there, you’re safe to begin. If your school participated, it is best to ask around any cybersecurity clubs on campus to see if you can get in touch with the previous team. This step is important not just to prevent duplicate applications, but to also establish a connection with your alumni, who can be crucial to your success.
Role of a Captain
CPTC asks teams to designate a captain and a co-captain as primary points of contact for the client throughout the season. Captain is not just a fancy title - there’s a lot of responsibility associated with it. Look at the table below and see for yourself how many things a captain is expected to do. I’ll be frank and admit up front that being captain can be stressful at times and it requires a lot from you, but it’s ultimately worth it. I was far from perfect on many of the points below, but the good news is that you don’t have to be perfect. You’ll have a team that has your back and all your work boils down to enabling them to do what they do best. As captain, you don’t have to be the most technically skilled person, in fact it’s better that you aren’t. Your job is to lead the team through the season and that means organizing, communicating and coordinating. I hope this blogpost helps you get started on that.
| Pre-Season | Mid-Season | Competition |
|---|---|---|
| Finding a Coach | Holding Practices | Leading the Penetration Test |
| Teaching a Bootcamp | Inviting Alumni | Completing Injects |
| Making Tryout Boxes | Communicating with Organizers | Doing Damage Control |
| Selecting a Roster | Travel Paperwork and Funding | Overseeing Report Writing |
| Sending the RFP | Coordinating Travel | Presenting to the Client |
Pre-Season
Finding a Coach
You are not allowed to compete in CPTC without a school representative supporting your team. In order for your team’s application to be considered, you need to find a professor who will sign the paperwork and assist you with administrative matters. It is important for a team to be student-driven and student-led, so the role of a coach does not necessarily mean leading practices and teaching the team. The coach should be there to give you guidance and be a trusted advisor, and most importantly be your liason between the school administration and the team.
When the competition moves back to fully in-person, you will need to travel to compete, therefore you will need funding for your flights and the competition organizers will reimburse only a part of it. This is where having a supportive faculty member coaching the team will be crucial. If you don’t know which professor to reach out to, see which faculty are cybersecurity club advisors at your school. If they are already supporting a student club, it means enabling student activities is important for them.
Teaching a Bootcamp
Pentesting is largely seen as a non-entry-level field for a good reason. There are a lot of important fundamentals that you need to know to be a good penetration tester. You need to be comfortable with a command-line, you need to understand Linux, Windows, have an idea about web applications and more. Looking for people who already know everything is really not a good strategy, because it misses an important reality - you can teach technical skills, but you can’t teach a work ethic or passion. The key to building the best possible team is to have a large audience and to give everyone an equal opportunity to learn, practice and share what they’ve learned.

You should create and teach an introduction course about penetration testing to anyone interested during the Summer. That is no small task, I know, but if you aren’t yet comfortable with every topic you need to teach, it will be a learning opportunity for you too and you’ll learn as you go. If you have friends that are able to help out, do enlist their help, because teaching alone is a lot of work. The reason you should teach the bootcamp during the Summer, is because it allows incoming Fall freshmen and transfers to join in as well.
Use any and all connections you can to spread the word about your bootcamp. Getting a large audience is key, therefore you should reach out to cybersecurity and technology clubs on campus to inform their members of the opportunity. If you can, you should reach out to your academic department and ask for your course to be featured in an email blast to all students within your major. This will most certainly go out to incoming freshmen and transfers, therefore it is very important.
Topics
There are many important topics that deserve to be taught as part of the bootcamp, but I recommend sticking to just around 6 to leave 2 weeks for the tryout. Saturdays are a good time to teach these, because most students don’t have classes, but it ultimately depends on your availability. If you teach every week, it will provide a good continuity for the people learning and it is best that you start with the basics and increase complexity every week. There’s an infinite number of possible topic combinations you can choose, but some topics are necessary, such as OSINT, Windows, Linux and Web Apps.
Homework
As much as we all hate it, we all know it’s necessary. Homework during a CPTC bootcamp is really not meant to be a test of people’s skill. The point of giving people homework is to see if they are organized and committed enough to be on the team. Someone who does no homework throughout the bootcamp and only shows up for the tryout can’t be trusted to be a reliable teammate, because CPTC is not just about the engagement days, most of the work and prep are done outside of them.
Leadership
You should put people in groups to work on labs and see how well they work together and if leaders emerge. CPTC is a team effort, therefore you do not want to see people just doing their part and then sitting back. The best teammates will be those that work together with others in their group, whether that means reaching an objective together, asking for help or teaching.
Holding a Tryout
The tryout at the end of the CPTC bootcamp is the culmination of all the training and the ultimate opportunity for those interested in joining the team to prove their skills. It is important that you allow and encourage those who don’t want to join the team to participate. Imposter syndrome is real prolific in infosec and people grossly misjudge their own skills and knowledge, therefore it is best that people participate even if they aren’t confident in doing well. Moreover, the bootcamp is also an opportunity for people to just learn and some might actually not be interested in competing. Those people will be grateful to have an opportunity to put what they’ve learned to practice.
Environment
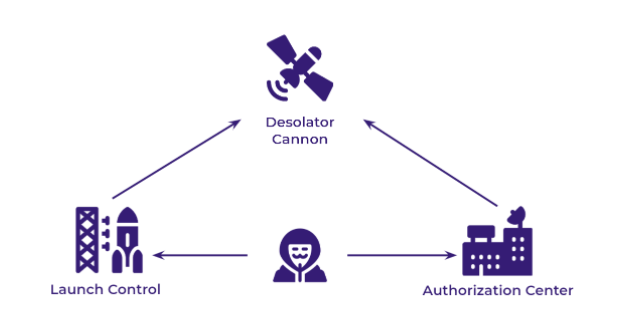
The vulnerable machines are at the core of the tryout. Think back to what you’ve done on HackTheBox and TryHackme and get creative - come up with a list of interesting vulnerabilities and implement them on a few machines. Think of a fictional company and come up with a scenario for your pentest. Have fun with it and make it interesting for those trying out. Add alternate exploitations path and let them run wild in the network. I’ve found three virtual machines to be the sweetspot, since most have enough RAM to run that many. See my example network topology below:
Access
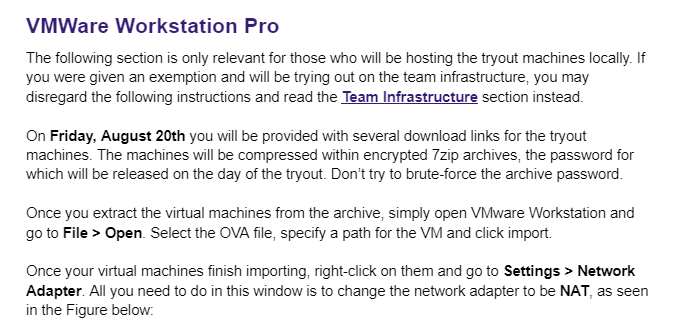
Chances are, you don’t have a datacenter all to yourself or thousands in credits on AWS or Azure, so the best way to have people access the tryout machines is locally with VMware or VirtualBox. The logistics of it are pretty simple - you probably get Office 365 through your school and for Cal Poly Pomona it includes a whole terrabyte of free storage. When you create your vulnerable machines, export them into OVA and zip them up with a strong password. You can then give out the download links the day before the tryout and release the Zip password the day of. See an example with instructions I shared with students:
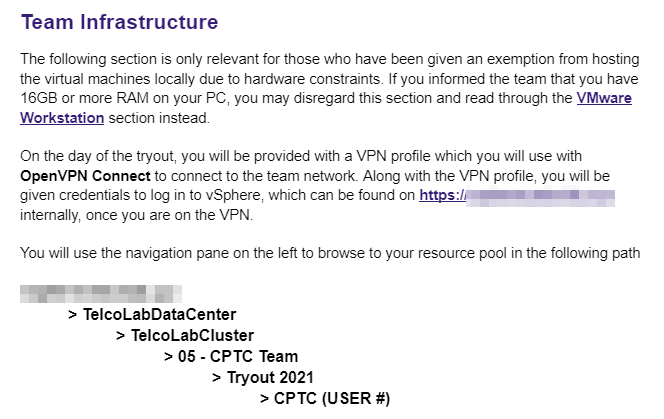
Sadly, it is a reality that not everyone has good enough hardware to run 3 or 4 virtual machines at once, but it can still possible for you to give them an equal playing field. Before the tryout, I surveyed everyone who was interested and identified that at most 5 people wouldn’t be able to run VM’s on their own. A cybersecurity club on campus was generous to provide access to their eSXI hypervisor and we hosted the extra environments on vSphere. You can see the student instructions for connecting to it below:
Deliverable
Just like in a real penetration test, competitors should produce a report as a deliverable. Figuring out a report template from nothing is a quick way to scare off many of the people trying out for the team, therefore I recommend giving them a generic template. Pentesters typically follow an established template, therefore it’s only fair. Below is an example of a very generic finding block that I made from some of the reports I’ve seen online. Please note that to win CPTC you’ll need something way more substantial than that.

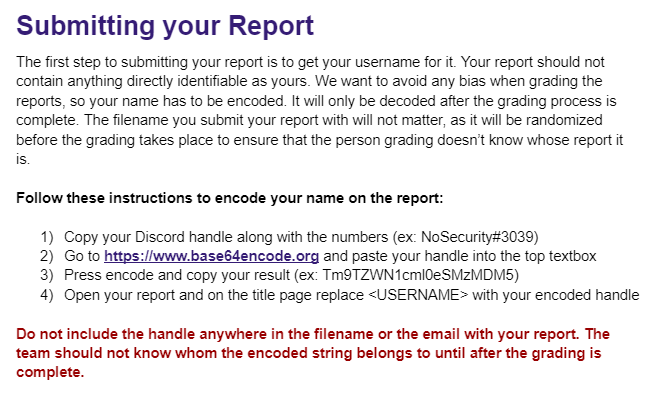
It is important to keep the tryout process impartial and free of bias, therefore you must take steps to make the grading mostly anonymous. I asked competitors to sign their report with their Base64 encoded username and to strip their deliverable of any other identifiable information. Since I was the only person grading, I’d need to honor the string secrecy regardless, so there was no point in going for actual encryption. If you have multiple people though, you can use symmetric encryption to limit the knowledge of decoded names to only one person.
Grading
The next step to making an impartial judgement of deliverable quality is having consistent grading, so a rubric is necessary. Grading technical findings is easy - just check the person’s list of findings against a master list of vulnerabilities you put into the environment. Grading the report is where it gets more complicated though. I had nearly 30 extensive reports to get through, so to simplify things a bit, I went with scoring just 4 categories of the report - summary, recommendations, steps and remediation. The rubric was shared with faculty to ensure everyone is on the same page and that we’re being as fair as possible to students. Look at my rubric below and create your own to suit the tryout.
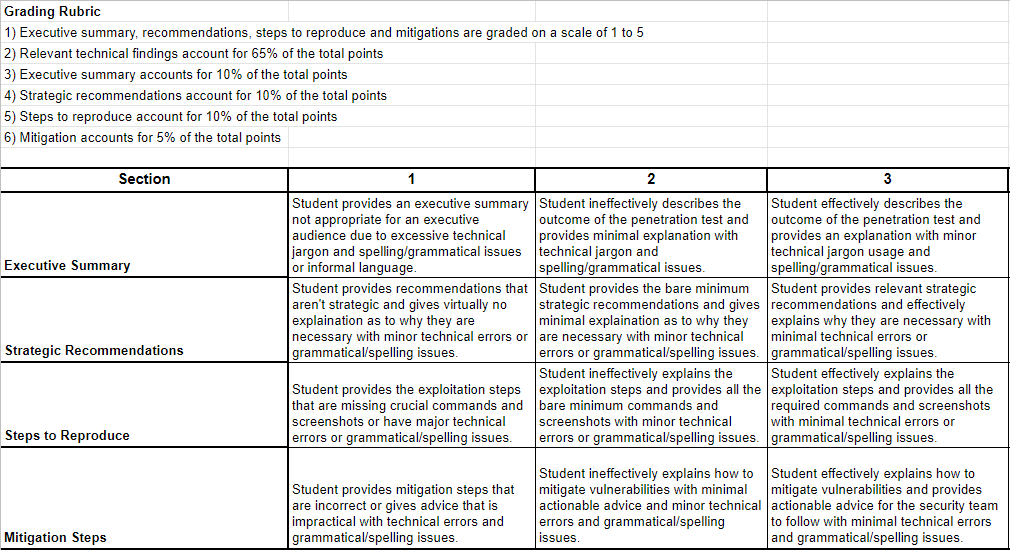
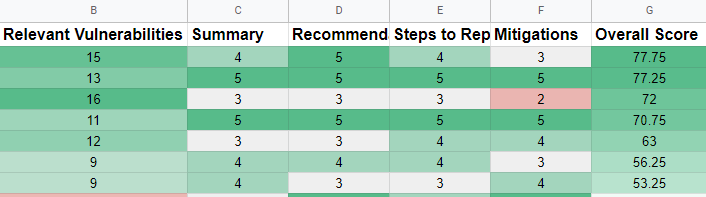
I went with an overall formula that put a lot of emphasis on the findings themselves. The relevant vulnerabilities accounted for 65% of total points, with summary, recommendations and steps for 10%, and lastly mitigation for 5%. I went through every report and graded it on the scales before decoding the student names and proceeding with the final grading.
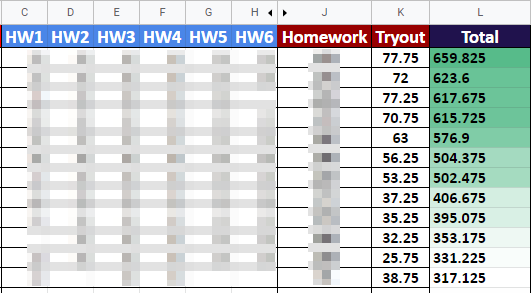
The final grade was a combination of homework and the tryout score, but I also recommend adding a measure of attendance and communication skills to it. The tryout score itself had the most weight obviously, but a significant lack of homework is still meant to be impactful enough to lower the scores for people who don’t do the work. See the final bootcamp scores table in the screenshot below. Homework scores are unique and therefore blurred to prevent individuals from being identified.
Doing the RFP
Once you select the final team roster from the scores, the RFP is your first opportunity to work as a team. An RFP is a Request For Proposal and it is document sent out by the client to seek penetration testing firms for the competition. You must treat it like a request from a real business and sit down with your team to develop a quality response to it in something like Google Docs. If you don’t submit the RFP on time or you submit a subpar response, you won’t go to CPTC. Spots are limited and therefore reserved for teams that are professional in their approach. Tailor your response to what the client asks and send it in the moment the RFP submissions open.
Conclusion
I hope what I’ve shared is helpful to you in starting your own CPTC team. This competition has been an invaluable experience for me as I hope it will be for you. Huge shoutout to the talented folks on the Cal Poly Pomona team, who are writing their own CPTC blogposts. Make sure to check them out if you wanna learn more: