CRTO-I Course and Exam Review
This week I passed the Certified Red Team Operator (CRTO) exam by RastaMouse from ZeroPointSecurity. Overall, this was a great follow-up to OSCP, because it took my Active Directory knowledge further and allowed me to practice with a real C2. It was well worth the money and every part of it was incredibly enjoyable. I highly recommend this course and exam to anyone interested in learning the fundamentals of red teaming and I’m publishing this to share my impressions and experiences with it.
The Course
I completed the course at a leisurely pace over 2 months after getting access and enjoyed the hell out of it. There’s so many reasons why this course is amazing and here are just a few that stood out most to me:
- All-Encompassing
- The course covers every phase of a red team engagement. From scoping and planning all the way to reporting. The focus is obviously on the technical topics though, which are all covered in detail. There is no other place where you can find all the red fundamentals with such quality and coverage. It works great as a reference and I recommend bookmarking it, because you’ll be going back to it even after you are done with the exam.
- Concise
- When you are a total beginner at something, it’s not always useful to dive into the lowest level of detail. It’s good to start with a high-level overview and then gradually build on top of it and increase the level of detail as you get more comfortable with the material. Rasta manages to teach all the topics in such a way that you aren’t overloaded with information, yet given enough detail to be able to understand and replicate the techniques.
- Well-Organized
- The course content is presented and organized extremely well. I much prefer Rasta’s website over any other platform/PDF for presenting content. Everything in the course is organized into different phases of a red team engagement, so it’s really easy to find material whenever you need it. If you know what you need to do, you can just refer to the appropriate section and you’ll find the course text and code clearly presented to you.
- Affordable
- Compared to a lot of other certifications and red team trainings, CRTO is very affordable. You don’t have to shill out thousands of dollars for access and you aren’t locked in to a certain number of days in the lab. You are free to extend it as much as you like and pay per hour. There’s a great deal of flexibility in how much you end up spending on it.
- Relevant
- See the next section.
Note on Real-World Applicability
The course is so good, I ended up using it as a reference in basically every internal pentest and red team engagement I’ve done so far as a junior consultant. From command reference to technique description, it’s super useful in the real world. Besides evasion (see CRTO-II instead), everything in the course was incredibly relevant. Rasta constantly updates the course as new techniques and tools come out, so the content is always up-to-date.
The techniques and tools presented in the course, if taken without modifications, will suit a real internal penetration test. If however you plan to participate in a red team exercise, you’ll have to substitute some of the tooling and modify some of the tradecraft from the course before you can be effective. For example, the Data Protection API section of the course relies heavily on mimikatz, which is guaranteed to get you caught. In a red team engagement you’d be better off using something like SharpDPAPI. The techniques stay the same, it’s just the tooling that in some cases needs to change.
The Labs
The lab access that comes with CRTO can be very helpful depending on your learning style. It’s basically a sandbox for you to test techniques or follow along with some of the course sections. Personally, I prefer challenge labs over sandbox labs, so I used up very little of my lab hours. On the exam Snap Labs dashboard there is a scoring tab that lets you submit flags and having something exactly like it in the lab would be terrific, in my opinion. Getting all the flags without referring to the course material should be a good indication that you are ready for the exam itself. It would definitely benefit from gamification.
Overall, I recommend spending more time in the lab rather than less and ensuring that you are comforatble with all the techniques and tools used on the exam, especially Cobalt Strike. If you aren’t an industry professional yet or you’ve never gotten to use it before on engagement, you must absolutely get familiar with it. Knowing the tools at your disposal in Cobalt Strike will make or break your exam attempt. If you can’t effectively use it, you won’t pass the exam.
Other Study Resources
HackTheBox RastaLabs
I initially purchased the RastaLabs pro-lab on HackTheBox (which I know Rasta no longer manages) to prepare for CRTO, since it seemed to align with the course pretty well, but I ended up disappointed. The problem with RastaLabs is that its Microsoft Defender is kept up-to-date. Bypassing updated Defender is not an insurmountable task by any measure, but it goes well beyond what CRTO is designed to be, which is, an introductory course about red team fundamentals.
It takes way too much effort to ensure smooth operations with Cobalt Strike in the current RastaLabs. CRTO-I is designed to merely introduce evasion as a topic, so obviously what you learn there is not enough to evade in the pro-lab. If you keep up to date with evasion, getting initial payload execution shouldn’t be an issue, however the pain really starts once you start doing post-exploitation. In CRTO using Cobalt Strike commands such as powershell or jump winrm is pretty much guaranteed to get your beacon killed. In RastaLabs the opsec-unsafe commands list is greatly expanded.
Don’t get me wrong, RastaLabs is a good pro-lab and it’s definitely doable, especially with a less signatured C2. It’s just not a great lab to prepare for CRTO specifically. Cobalt Strike is a huge part of CRTO and losing the ability to practice with it will be a big detriment. At the same time, if you are already so comfortable with evasion that the basic defenses of RastaLabs aren’t a problem for you, then CRTO is probably going to be way too easy for you.

CyberSecLabs Active Directory
I’m a little confused why people recommend the CyberSecLabs Active Directory boxes to prepare for CRTO. They are great for learning the basics of Active Directory and are decent overall, but they won’t directly help you in CRTO. They are nothing like the exam boxes. I completed all the AD labs in less than a week when I was preparing for OSCP and I found that they were pretty good in prepping me for that cert, but not for this one.
The Exam
Exam Logistics
I have nothing but positive things to say about everything around the exam logistics. Booking the exam was super easy and there were plenty of spots. In fact, I scheduled my exam for the same day and had no trouble getting a spot. This comes in contrast to other popular certs, which if you want to do over a weekend, you have to book weeks, if not months in advance. You can also reschedule as much as you want in case something comes up.
Exam Length
The fact that you have 4 days to complete the exam is such a blessing. 24 hours of continuous hacking is a tall order when you have a life with things like work, family, friends and responsibilities. Not only can it be logistically impossible, but it’s also just not healthy or realistic. It’s so nice that RastaMouse recognizes that and still allows for that flexibility to continuously hack up to 48 hours if you want to. But even then, you can still pause it and not have your 48 hours tick down if you’re getting rest.
Proctoring and Reporting
But wait, the upsides don’t end there, because there is also zero proctoring on the exam. You don’t have to feel uncomfortable in your own home because you are getting watched for 24 hours straight and have to ask for permission to use the bathroom. Moreover, you don’t have to turn a report in after your exam, because it’s meant to test technical skills.
Exam Access
Finally, exam provisioning was absolutely pain-free. There are no buggy extensions you have to install in your browser and no VPN to troubleshoot. You don’t even have to show your entire room or point your webcam under your desk. You get Snap Labs when you buy the course and the exam network appears in your account the day of your exam. You just can’t power on the machines until your allotted time. You can then use the Snap Labs dashboard during the exam to reset flags, machines, credentials, etc. Having that flexibility to fix an exam network that broke is incredibly useful.
My Performance
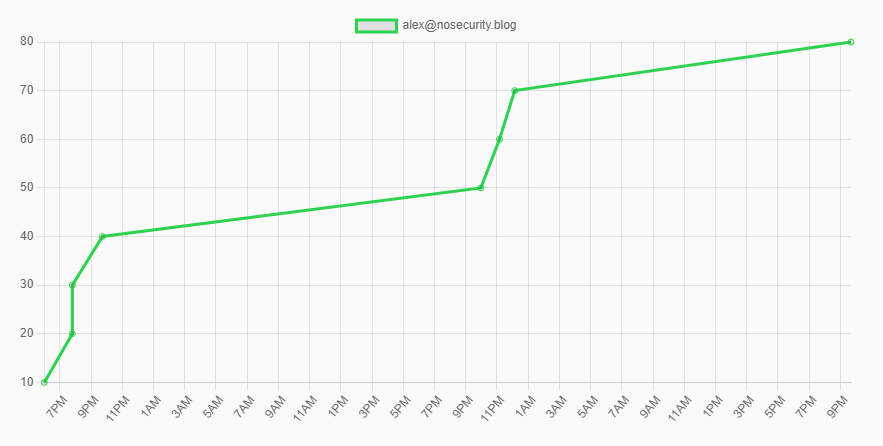
I had decent success with the exam, because I was able to get all the flags in about a third of the time allocated for the exam. The first few flags were obviously a breeze, but the exam really picked up in difficulty after flag 4. I found the 6 flags needed to pass after using up 12 hours of my exam time and then got the last 8th flag about 14 hours in.
It’s worth noting that I made the impulsive decision to take this exam in the middle of a work week, because I just couldn’t wait till the weekend, so I ended up hacking for about 14-16 hours a day. I’d come back home from 8-10 hours of work and then do 6 hours on my exam for 2 days in a row. I took just about 2 hours on my last day to regain my access, take detailed notes and hit the last flag.
Needless to say, I was not in an optimal state, so my guess is that I would have done much better time-wise, had I booked it for a weekend. A solid third of my time was spent regaining my access and troubleshooting issues I created for myself because I was exhausted. One day I’ll stop booking exams for stupid time slots.
Exam Difficulty
RastaMouse’ approach to creating the exam is amazing. What you learn in the course is actually directly applicable to it. The things you see in the lab are there too. So refreshing to see a course that actually tests you on the things it teaches you vs. throwing curveballs at you, hoping you pay for a retake. The beauty of this exam is that the course itself is enough to pass it. It isn’t difficult at all.
It also isn’t a spoiler to say that pretty much every topic taught during the course is covered on the exam. Every topic is important to learn and practice, however some are more important than others. I especially recommend you to be comfortable with the following sections of the course and the lab (in no particular order):
- Kerberos
- Lateral Movement
- Pivoting
- Credential Theft
- MSSQL
Technical Issues
There was a plethora of technical issues I ran into during the exam, most of which really boil down to infrastructure problems, which are inherent to the way the exam is hosted and offered. One night I deployed the environment and had a multiple-second delay communicating between the Windows attack box to the Linux attack box hosting Cobalt Strike. This made running any command on any of my beacons an absolute pain. Other times I’d have beacons die even when I’m not doing anything on the exam network, just to come back 5-15 minutes later. Having helped host a large network on AWS in the past, I really can’t blame RastaMouse over this. If anything, I’m surprised it works as well as it does.
Here’s some advice to avoid having the technical issues bog you down:
- Make sure to click the
Cache Credsbutton inside your Snap Labs dashboard to ensure you aren’t missing credentials - If you see that a flag is missing on the Administrator’s desktop after you compromise a machine, reboot the
AdminBoxin Snap Labs- Shoutout to Dylan for letting me know about this one
- If your beacons die for no reason, take a little break. Computers need rest too, so they might just come back.
- And if not, it’s still worth it, because it helps distract you from being frustrated over losing your progress
Conclusion
Just to restate this again, CRTO is an amazing course and exam. I highly recommend it to anyone new to red teaming. And as far as next steps for me go, the short answer is - idk man. Regardless, I will eventually complete CRTO-II and post a blogpost for that too. In general, you should expect my blog to now have a more steady content output, because I am dedicated to completing at least one certification every quarter.
Credits
Special thanks to some of the people who inspired me to take this course and supported me throughout:
And most importantly, thanks to the man himself:
